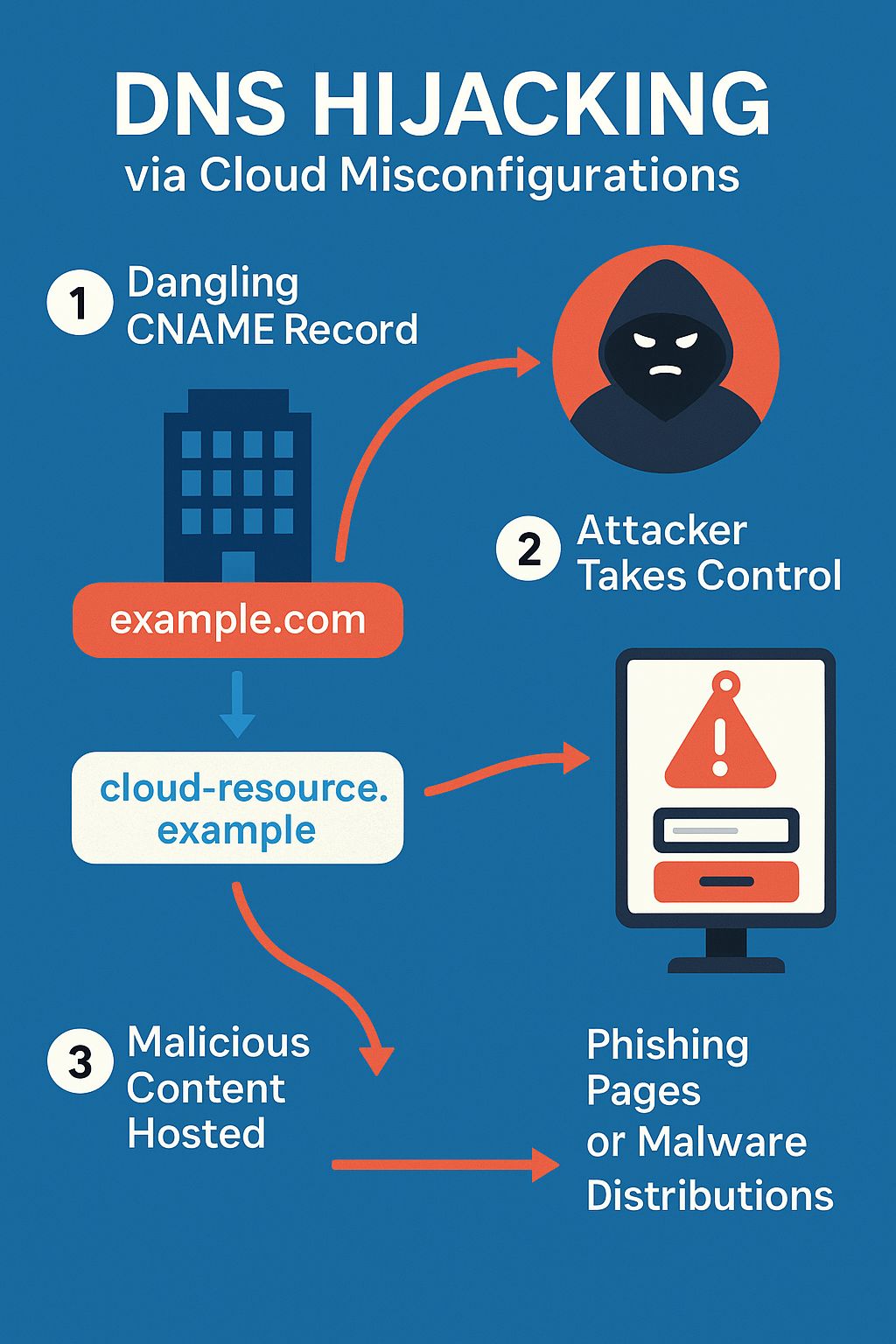
DNS Hijacking Campaign by ‘Hazy Hawk’ Puts Major Organizations at Risk
A newly identified cybercrime group is exploiting abandoned cloud infrastructure to hijack subdomains and launch malicious campaigns under the names of trusted organizations. This threat actor, known as Hazy Hawk, is using overlooked DNS configurations to target enterprise brands and government entities alike—highlighting a growing blind spot in cloud security [...]