A newly identified cybercrime group is exploiting abandoned cloud infrastructure to hijack subdomains and launch malicious campaigns under the names of trusted organizations. This threat actor, known as Hazy Hawk, is using overlooked DNS configurations to target enterprise brands and government entities alike—highlighting a growing blind spot in cloud security management.
How the Attack Works: DNS Hijacking via Cloud Misconfigurations
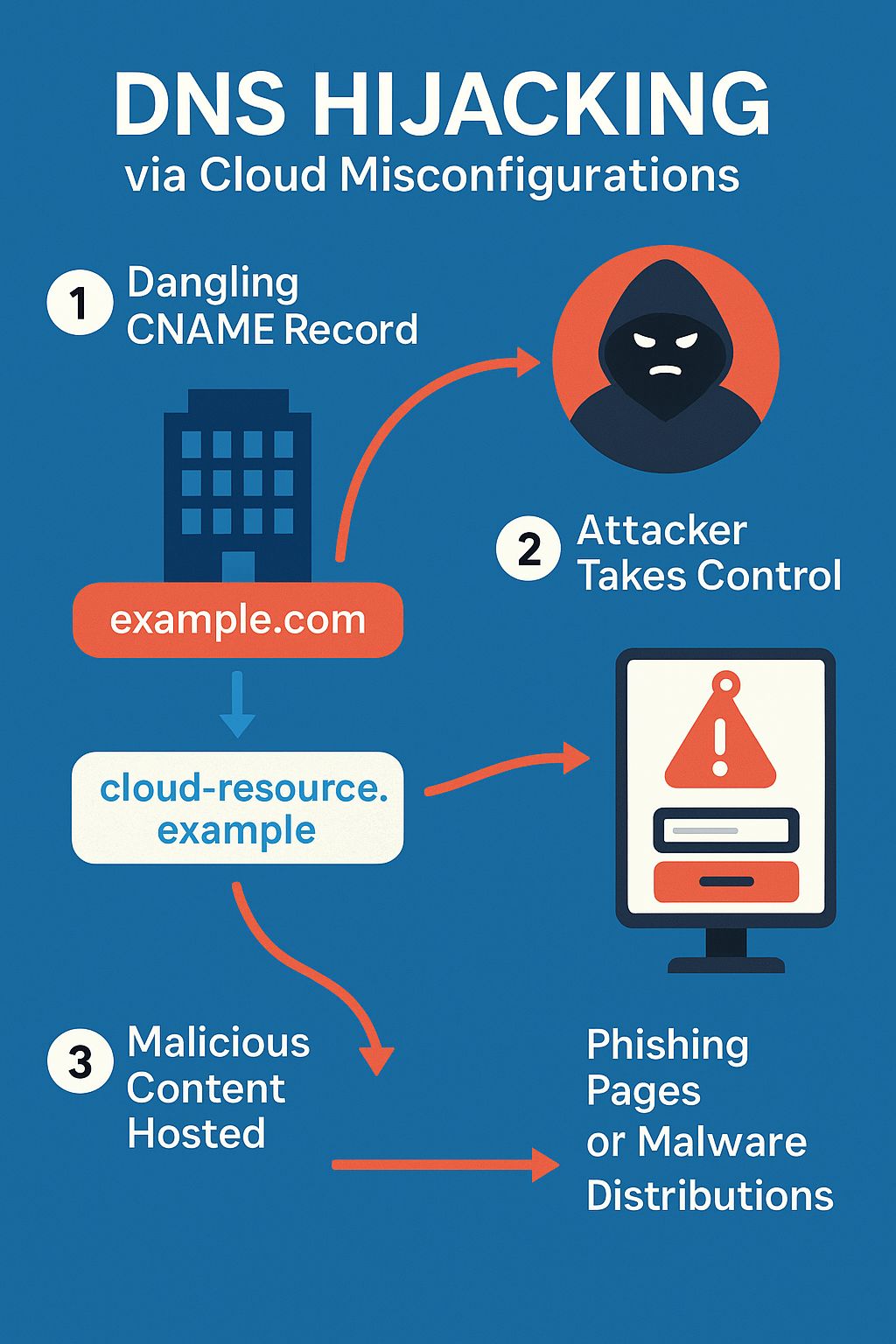
Hazy Hawk leverages a technique involving dangling CNAME records—DNS entries that point to cloud-based resources (like Azure apps or AWS S3 buckets) that no longer exist or have been decommissioned. When an organization forgets to remove or update these records, attackers can claim the underlying cloud resource, effectively taking control of the domain or subdomain it points to.
Once hijacked, the attackers can use these domains to host malicious content, phishing pages, or redirect users through traffic distribution systems (TDS) to scams or malware—without ever compromising the core infrastructure of the victim organization.
Notable Victims and Scope of Impact
Among those impacted by this technique are high-profile entities including:
- The U.S. Centers for Disease Control and Prevention (CDC)
- Big Four accounting firms like Deloitte, PwC, and Ernst & Young
These compromised subdomains, although technically “abandoned,” still retain trust with users and automated systems, making them ideal for spreading malware, social engineering schemes, or deceptive pop-ups that trick users into enabling notifications or downloading software.
Why This Threat Matters
Attacks like this are especially dangerous because they:
- Exploit legitimate infrastructure: No exploit is required—just overlooked DNS records.
- Bypass perimeter defenses: Traffic appears to come from trusted domains.
- Impact brand reputation: Even though the core systems aren’t breached, the organization’s name is used to mislead users.
- Target supply chains: A single hijacked subdomain could affect customers, partners, and vendors.
This represents a classic case of security by omission—where gaps in routine cloud hygiene create unintentional risk exposure.
How to Protect Against Cloud DNS Hijacking
To defend against attacks like those executed by Hazy Hawk, organizations should prioritize the following security practices:
1. Regular DNS Hygiene
Conduct routine audits of your DNS records, especially CNAME entries pointing to cloud services. Remove or update any that reference unused, expired, or decommissioned infrastructure.
2. Centralized Cloud Asset Inventory
Use asset management tools to maintain an accurate inventory of active cloud services and their associated DNS configurations.
3. DNS Filtering and Protective Services
Deploy DNS security solutions that can detect and block access to known malicious redirectors or domains hosted by third parties.
4. Educate End Users
Train staff to recognize unusual redirects, unsolicited popups, and browser-based permission requests tied to notifications or downloads.
5. Monitor for Subdomain Takeover
Use automated tools or third-party services to monitor your domains for takeover risks. There are open-source and commercial solutions that alert on dangling DNS entries.